Israeli cybersecurity researchers have disclosed details about a new flaw impacting DNS protocol that can be exploited to launch amplified, large-scale distributed denial-of-service (DDoS) attacks to takedown targeted websites.
Called NXNSAttack, the flaw hinges on the DNS delegation mechanism to force DNS resolvers to generate more DNS queries to authoritative servers of attacker’s choice, potentially causing a botnet-scale disruption to online services.
“We show that the number of DNS messages exchanged in a typical resolution process might be much higher in practice than what is expected in theory, mainly due to a proactive resolution of name-servers’ IP addresses,” the researchers said in the paper.
“We show how this inefficiency becomes a bottleneck and might be used to mount a devastating attack against either or both, recursive resolvers and authoritative servers.”
Following responsible disclosure of NXNSAttack, several of the companies in charge of the internet infrastructure, including PowerDNS (CVE-2020-10995), CZ.NIC (CVE-2020-12667), Cloudflare, Google, Amazon, Microsoft, Oracle-owned Dyn, Verisign, and IBM Quad9, have patched their software to address the problem.The DNS infrastructure has been previously at the receiving end of a rash of DDoS attacks through the infamous Mirai botnet, including those against Dyn DNS service in 2016, crippling some of the world’s biggest sites, including Twitter, Netflix, Amazon, and Spotify.
The NXNSAttack Method
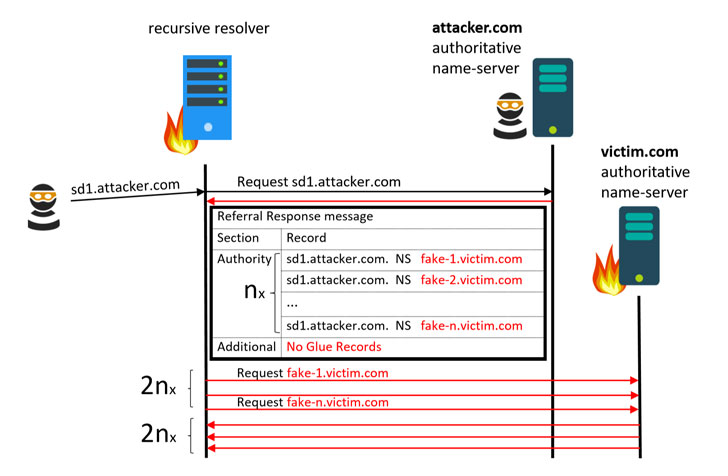
A recursive DNS lookup happens when a DNS server communicates with multiple authoritative DNS servers in a hierarchical sequence to locate an IP address associated with a domain (e.g., www.google.com) and return it to the client.
This resolution typically starts with the DNS resolver controlled by your ISPs or public DNS servers, like Cloudflare (1.1.1.1) or Google (8.8.8.8), whichever is configured with your system.
The resolver passes the request to an authoritative DNS name server if it’s unable to locate the IP address for a given domain name.
But if the first authoritative DNS name server also doesn’t hold the desired records, it returns the delegation message with addresses to the next authoritative servers to which DNS resolver can query.
In other words, an authoritative server tells the recursive resolver:
Ontario’s New Privacy Impact Assessment Requirements: What You Need to Know
November 2025, A Major Shift in Privacy Compliance If your organization is a provincial go…