
In a development security pros feared, attackers are actively targeting yet another set of critical server vulnerabilities that leave corporations and governments open to serious network intrusions.
The vulnerability this time is in BIG-IP, a line of server appliances sold by Seattle-based F5 Networks. Customers use BIG-IP servers to manage traffic going into and out of large networks. Tasks include load balancing, DDoS mitigation, and web application security.
Last week, F5 disclosed and patched critical BIG-IP vulnerabilities that allow hackers to gain complete control of a server. Despite a severity rating of 9.8 out of 10, the security flaws got overshadowed by a different set of critical vulnerabilities Microsoft disclosed and patched in Exchange server a week earlier. Within a few days of Microsoft’s emergency update, tens of thousands of Exchange servers in the US were compromised.
Day of reckoning
When security researchers weren’t busy attending to the unfolding Exchange mass compromise, many of them warned that it was only a matter of time before the F5 vulnerabilities also came under attack. Now, that day has come.
Researchers at security firm NCC Group on Friday said they’re “seeing full chain exploitation” of CVE-2021-22986, a vulnerability that allows remote attackers with no password or other credentials to execute commands of their choice on vulnerable BIG-IP devices.
“After seeing lots of broken exploits and failed attempts, we are now seeing successful in the wild exploitation of this vulnerability, as of this morning,” Rich Warren, Principal Security Consultant at NCC Group and co-author of the blog wrote.
In a blog post NCC Group posted a screenshot showing exploit code that could successfully steal an authenticated session token, which is a type of browser cookie that allows administrators to use a web-based programming interface to remotely control BIG-IP hardware.
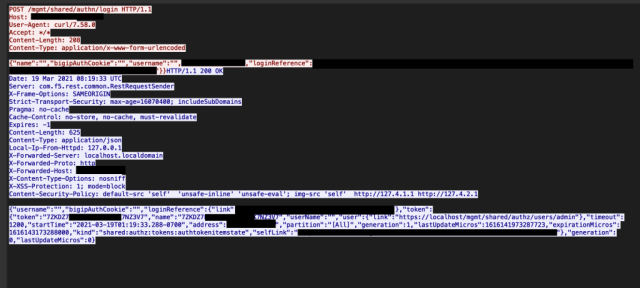
“The attackers are hitting multiple honeypots in different regions, suggesting that there is no specific targeting,” Warren wrote in an email. “It is more likely that they are ‘spraying’ attempts across the internet, in the hope that they can exploit the vulnerability before organizations have a chance to patch it.”
He said that earlier attempts used incomplete exploits that were derived from the limited information that was available publicly.
Security firm Palo Alto Networks…
Ontario’s New Privacy Impact Assessment Requirements: What You Need to Know
November 2025, A Major Shift in Privacy Compliance If your organization is a provincial go…














