In this article, we hope to break down some of the numbers and gain insight into the nature of these attacks, where they originate from, and who they’re targeting.
Key observations
- Between 2009 and 2018 there was a 440% increase in global cyberwarfare attacks.
- 30% originated in China or Russia.
- 26.3% targetted the USA.
- 27% of attacks on the USA occurred in 2018.
Chapters
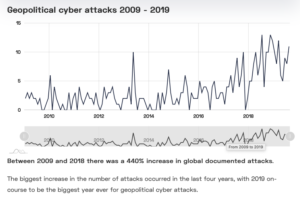
Between 2009 and 2018 there was a 440% increase in global documented attacks.
The biggest increase in the number of attacks occurred in the last four years, with 2019 on-course to be the biggest year ever for geopolitical cyber attacks.
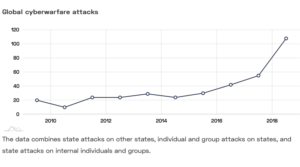
Global cyberwarfare attacks
The data combines state attacks on other states, individual and group attacks on states, and state attacks on internal individuals and groups.
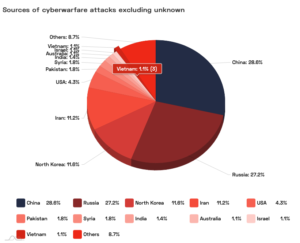
Biggest sources of cyberwarfare attacks 2009-2019
By far the biggest actors on this scene are China and Russia, with almost 35% of Global attacks originating in either China or Russia. There have been 79 confirmed attacks on national governments that have originated in China, and 75 in Russia.
Next is North Korea and Iran, sharing 16% of global attacks, followed by the USA, where 3% of global attacks originated.
It’s extremely important to remember here, that due to the very nature of cyberwarfare and cyberespionage, many attacks go under the radar, so we don’t tend to hear about them.
Sources of cyberwarfare attacks excluding unknown
An interesting case is the apparent use of the Eternal Blue vulnerability that the NSA developed tools to exploit. These tools were detected by China and subsequently used during the massive ransomware attack on Baltimore in 2019. Of course questions have to be asked of the NSA, but – Microsoft patched this vulnerability in 2017, and Baltimore officials simply ignored it and failed to update their computers.
Now, it wasn’t until the NSA discovered that their tool had been used to develop ransomware that they alerted Microsoft to the critical vulnerability, so without that we would never have known about their attacks on China.
Attacks originating in China 2009 – 2019
Between 2009 and 2019 there have been…
Ontario’s New Privacy Impact Assessment Requirements: What You Need to Know
November 2025, A Major Shift in Privacy Compliance If your organization is a provincial go…